b01lers CTF 2024
Writeups for solved b01lers CTF 2024 challenges
points: 2366 rank: 61/393
misc
misc/wabash
wabash, its a river, but also a new shell! Flag is in /flag.txt
Shell challenge - it adds wa on start of each command and arguments seperated with spaces so commands and args will not work. Example input:
cat /flag.txt > wacat wa/flag.txt
Solution: |cat</flag.txt
flag: bctf{wabash:_command_not_found521065b339eb59a71c06a0dec824cd55}
misc/bash cat with pipe
It allows commands. but certain characters and words are getting filtered out like ()""$*? among others. Also, the word flag is not allowed as input.
Solution:
cat {f,}lag.txt
flag: bctf{owwwww_th4t_hurt}
misc/chest-mix
Here’s a minecraft world, the flag is on a piece of paper in the the chest by spawn, it’s hard to miss. Version 1.20
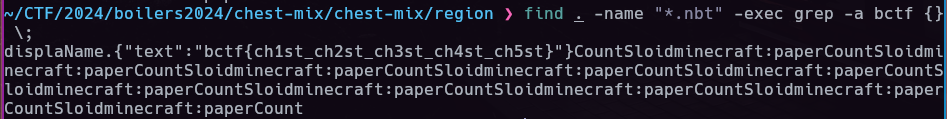
We are given Minecraft world save file, look for ways to parse this. I found a chunk extractor script that can extract contents from a region save. From there we can grep each region for any minecraft chunk/block we want.
https://github.com/sudofox/minecraft-utils/blob/master/region-parser/region-parser.sh
|
|
web
web/b01ler-ad
#xss/blind #filter-bypass
XSS challenge - We are allowed to input any html data we want and the admin visits that but the content should not contain quotes, double quotes and backticks:
Main challenge
|
|
We can use String.fromCharCode https://charcode98.neocities.org/ to avoid using quotes and encode our URL before sending it to the admin. Admin visits our site with their cookies in the query.
|
|
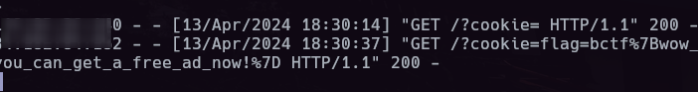
flag: bctf{wow_you_can_get_a_free_ad_now!}
web/3-city-elves-writeups
#command-injection/blind #filter-bypass
Command Injection challenge where we need to bypass a blacklisted words and leak a flag.png. To solve this I setup a file upload server after confirming i can do a curl command.
Main challenge
|
|
waf.py
|
|
We can bypass most of the linux command words using this technique c''url and to bypass the / we can do ${HOME:0:1}. https://book.hacktricks.xyz/linux-hardening/bypass-bash-restrictions
The command I used does a POST request to my file upload server with the /flag.png attached in the body
solve.py
|
|
server.py
|
|
To view the flag, I just opened the uploaded file under /uploads on the listener server

flag: bctf{Lucky_you_I_did_not_code_this_stuff_in_Ruby_lasudkjklhdsfkhjkae}
rev
rev/Annnnnnny Second Now
Analyze in ghidra and learn that the super_optimized_calculation is not so optimized. It just returns the nth fibonacci number
We can just hardcode it and run it will print the flag
|
|
flag: bctf{what’s_memoization?}
rev/js-safe
#js #deobfuscation
The original file provided is obfuscated. which can be deobfuscated here: https://obf-io.deobfuscate.io/
The main challenge is under addToPassword function doing comparisons and operations.
Basically, It just checks the index if it matches with the corresponding operation on the right. If we start from the button we will know that arr[3] = 82 and then work up from there. 82 ^ 0x36 = 100 etc..
|
|
After getting the key p4wR0d we can just decrypt it using the following:
|
|
flag: bctf{345y-p4s5w0rd->w<}